Today, it is hard to imagine any business sector that does not utilize IT. It plays a huge role in banking, industry, transportation, agriculture, etc. Each industry has its own specifics, and it is not always possible to find a ready-made application that would fully meet the needs of a particular organization. At the same time, many developers deliberately neglect the requirements of safe code development in pursuit of deadlines and profit.
This article discusses the SDLC & SSDLC concept, Owasp SAMM, and top developer security practices.
SDLC concept
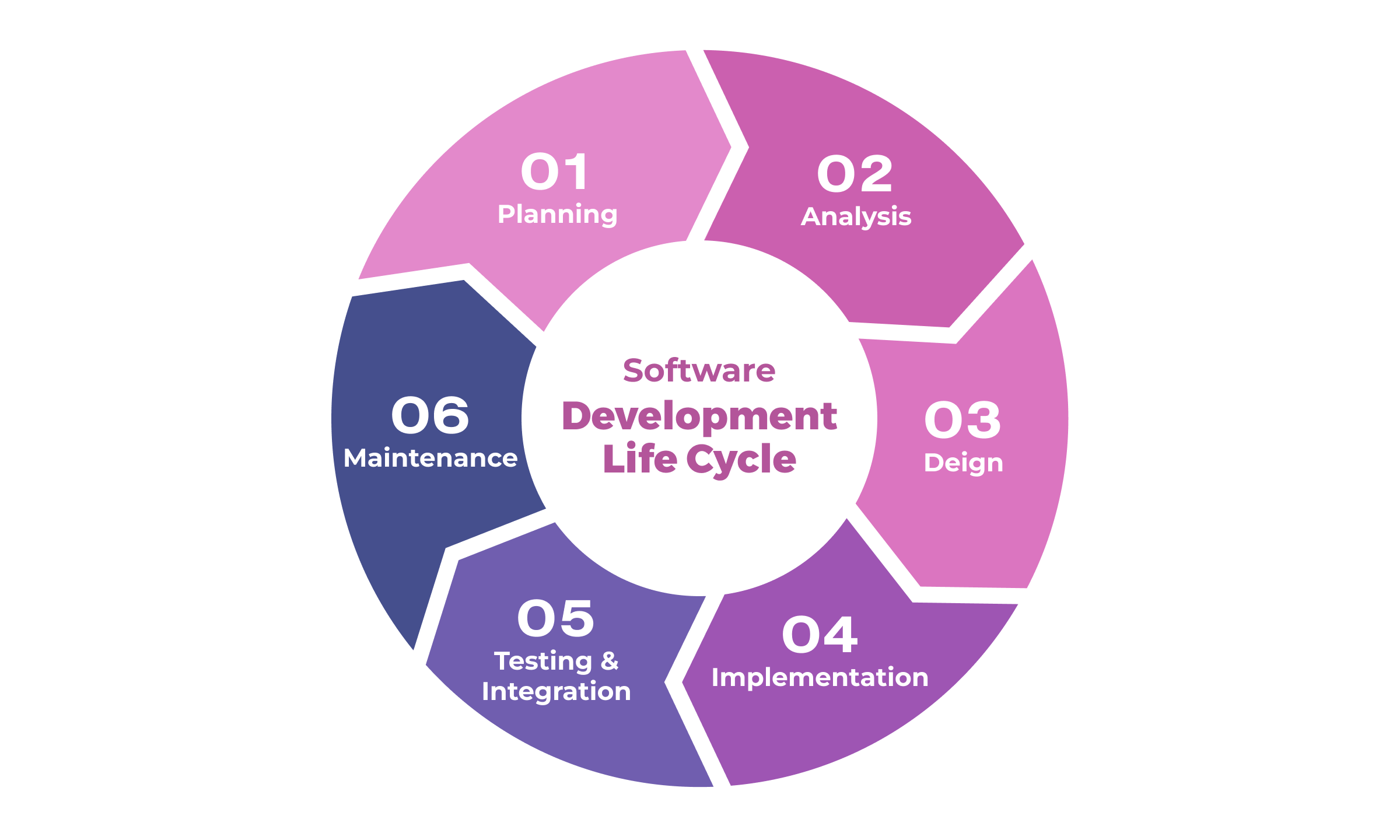
Software Development Life Cycle (SDLC) is a systematic process used by software developers to design, develop, test, and deploy software applications or systems. It consists of software product development steps. This concept consists of the following six steps:
- Requirements analysis
- Planning
- Design and engineering
- Software development
- Testing
- Deployment
Various models exist for implementing the SDLC, including the Waterfall model, Agile model, Iterative model, Spiral model, and others. Each model has its strengths and weaknesses, and the choice of model depends on the specific project requirements and constraints. Agile methodology is known for its flexibility and adaptability, while the Waterfall model is more linear and structured.
Waterfall SDLC
Consistent execution of all the above steps is assumed in the Waterfall methodology. This methodology is simpler and more manageable. At the same time, it is successfully applied only in those projects where any project requirements do not change significantly during development.
However, adhering to the original requirements when developing serious custom web applications is challenging. During the specific step, many things can change, both in technology (new versions or updates for OS and software) and in the customer’s business (merger with another company, IPO). Force majeure circumstances, such as sanctions, may also appear.
That is why Agile methodology is more popular in modern software development.
Agile SDLC
The general essence of Agile methodology can be described in the following words: a working product is more important than comprehensive documentation, cooperation with the customer is more important than negotiating contract terms, and readiness to change is more important than following the original plan.
Agile methodology suits software products with frequently changing business requirements and no specific reliability requirements.
SSDLC concept
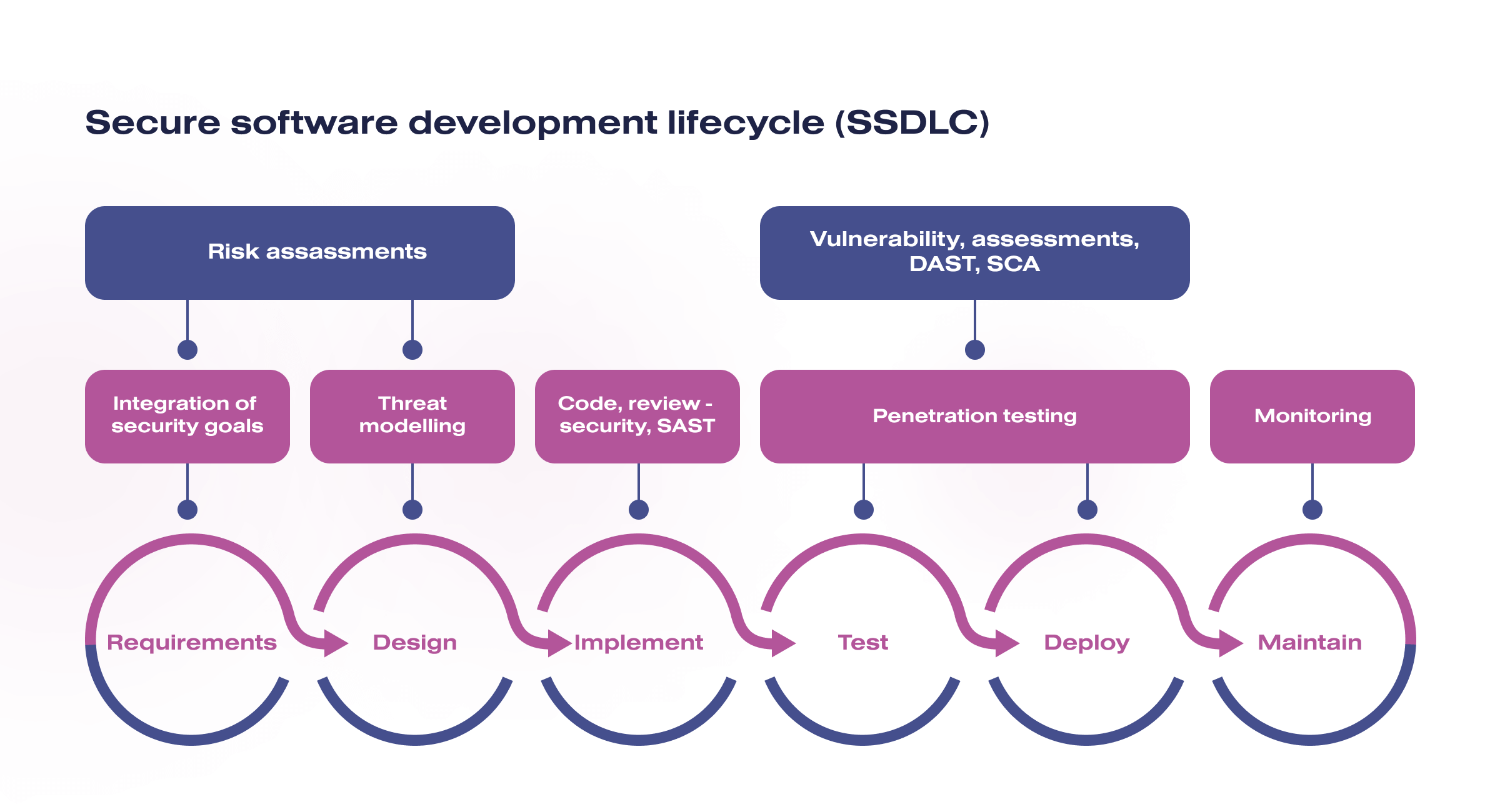
SSDLC (Secure Software Development Lifecycle) is a development concept that ensures the security of the developed application, risk identification, and management.
At the same time, this concept implies performing several steps before developing a software product. Thus, before the start of development, the whole team should pass Pre-SDL: Security Training.
Since the team members’ training levels may differ significantly, surveying employees’ knowledge of security and data protection topics is necessary. Based on the collected data, a training system should be developed to maintain software security. The following topics should be covered during the training:
- Security engineering
- Threat modeling
- Secure development
- Security software testing
- Ensuring privacy
The team can start development only after completing the training and successfully passing the tests on these topics.
The main problem with this approach is that it is impossible to implement the concept step by step as described in the document. As mentioned above, each team in the company already has a level of maturity in information security that is required:
- To raise simultaneously across multiple teams
- To raise comprehensively
And each successive maturity level is more complex than the previous one. You can assess a company’s information security maturity level using the Owasp SAMM framework.
Owasp SAMM
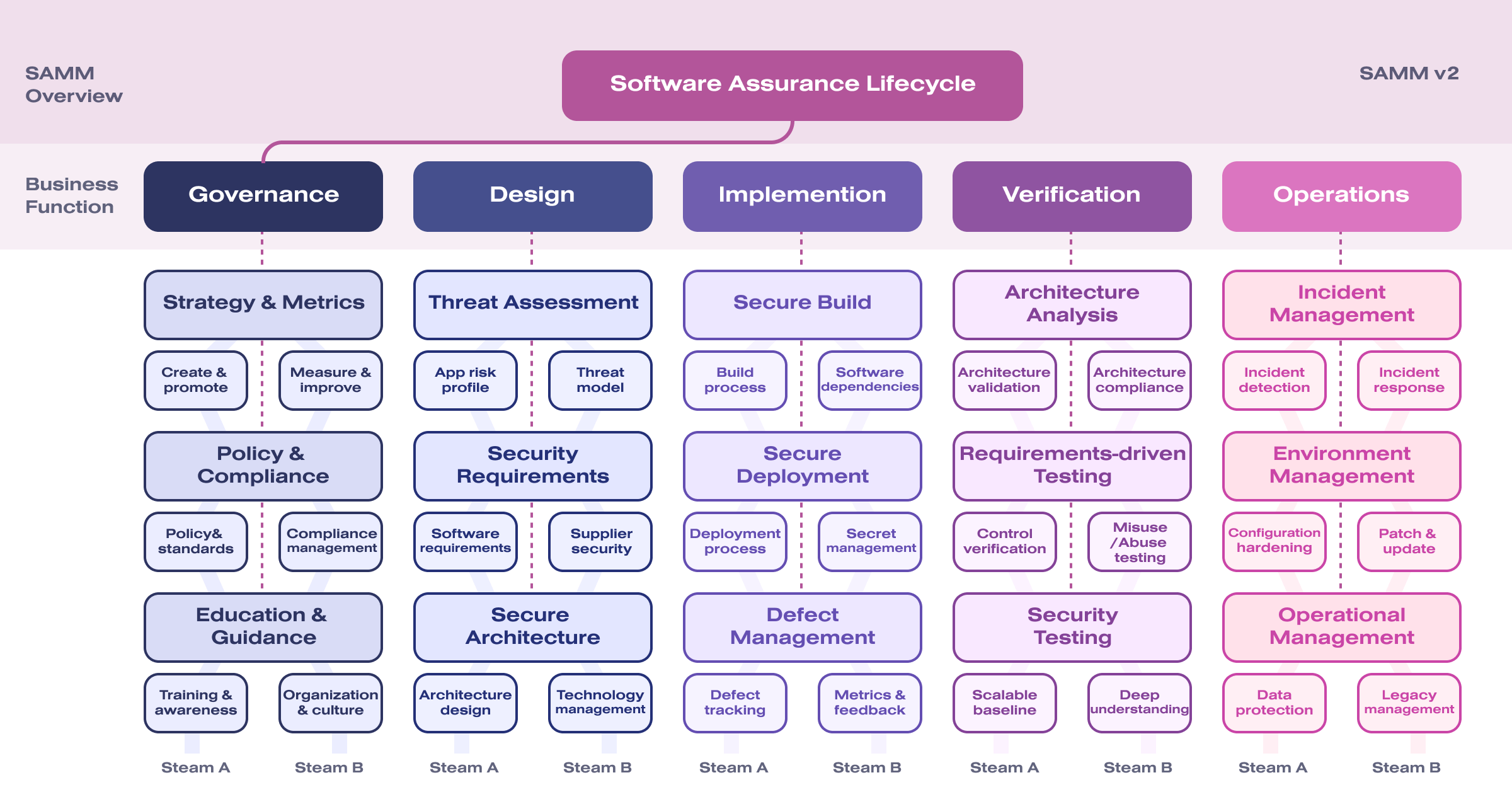
Software Assurance Maturity Model (SAMM) allows you to assess the maturity level at each iteration of development in the company. It also offers a set of methods to improve it. The framework consists of 5 business functions:
- Governance
- Design
- Implementation
- Verification
- Operations
In total, nearly 100 questions need to be answered. Based on the results of the answers, a score is calculated for each domain. There are online calculators such as Concord | SAMM 2.0 Calculator to automate the assessment.
Based on the results, you can assess the level of development maturity in the company and understand in which of the given areas it is necessary to conduct additional training of developers.
5 Top Developer Security Practices
Here are 5 top security practices we employ at SoloWay Tech.
Make security your software’s foundation
Prioritizing application security is not just a step – it’s the cornerstone of your software development. Embed security seamlessly into every phase of your software development lifecycle, ensuring a fortified defense from inception to completion.
Adopting secure software development lifecycle techniques is pivotal. Evaluate security intricately during planning, design, development, bug fixing, maintenance, and project completion. Elevate the safety of your SDLC with simple yet impactful measures. For instance, you should advocate using pre-commit hooks as security safeguards, preventing the accidental exposure of sensitive information in source code repositories.
Establishing project security imperatives
Safeguarding your project begins with meticulously examining potential security gaps and weaknesses. Consider these guidelines to define and fortify your project’s security requirements:
- Multi-core secure software design. Embrace a multi-core secure software design to anticipate and address unknown and unforeseen interactions between processes and threads. This proactive approach serves as a robust foundation against potential vulnerabilities.
- System resilience. Bolster your system’s resilience against intentional and unintentional failures. Cybercriminals often exploit vulnerabilities by overloading and flooding systems with fake queries to disrupt manageability. Strengthen your defenses to thwart such attempts effectively.
- Hierarchical user rights. Devise a meticulously planned hierarchy of user rights (project roles) to grant limited access based on individual responsibilities. This ensures that each team member has precisely the level of access required, enhancing security by minimizing potential points of exploitation.
- Process operation constraints. Impose constraints on how different processes operate and behave. Doing so creates a protective barrier, preventing hackers from interfering with the entire system and causing extensive damage, even in the event of an attempted takeover.
Prioritizing these measures defines and fortifies your project’s security posture, laying a resilient foundation for development and beyond.
Unveil and neutralize security risks proactively
Collaborate closely with your development team to uncover potential security threats linked to the tools in use. This crucial step precedes the commencement of the development process, laying the groundwork for a robust security posture.
Inscribe a defensive mindset into your code-writing endeavors, fortified by comprehensive unit testing across every conceivable vulnerability. Moreover, instill a practice of code audit whenever changes are made. This diligent approach ensures that each modification is scrutinized for potential security vulnerabilities.
Establish robust secure coding protocols
Every organization must formulate its unique set of secure coding guidelines. The specifics of these guidelines will naturally be tailored to the requirements of your project. However, their overarching goal remains steadfast – safeguarding all forms of data.
A stringent shield must be in place whether data is in transit or at rest. This encompasses the protection of cookies, sessions, file storage, and database repositories. Employ encryption services as a formidable tool to cloak data, ensuring its imperviousness to prying eyes.
A strategic approach to crafting secure coding guidelines involves aligning with industry security standards. These standards, integral to the tech landscape, serve as a blueprint for organizations to embrace superior design principles.
Utilize cutting-edge frameworks and libraries
The arsenal of frameworks and libraries is diverse. Opt for well-established, diligently maintained, and trusted frameworks and libraries, as they typically harbor fewer security vulnerabilities than their developing counterparts.
Using open-source software components offers the advantage of early bug detection, affording you greater control over your software’s security landscape. Secure libraries, in particular, play a pivotal role in constricting the potential attack surface of your system.
Before integration, developers should meticulously scrutinize the reputation of a framework or library. A prudent practice is to subject every new addition to human approval.
Conclusion
Beyond the realm of code composition, secure software development encompasses the entire lifecycle – from conception to delivery. To fortify your organizational foundation, adopt a holistic approach that intertwines secure development practices seamlessly into your daily workflow.
By ingraining security into the everyday workflow, you fortify the resilience of your entire development ecosystem, creating a culture where safeguarding digital assets is everyone’s commitment.




